Repository hinzufügen:
wget -q -O - https://pkg.jenkins.io/debian/jenkins.io.key | sudo apt-key add -
sudo sh -c 'echo deb http://pkg.jenkins.io/debian-stable binary/ > /etc/apt/sources.list.d/jenkins.list'sudo apt update
Installiere und starte Jenkins
sudo apt install jenkins
sudo systemctl start jenkinssudo systemctl status jenkins
Firewall öffnen!
ufw allow proto tcp from Youre IP to any
ufw allow from Your IP any port 443
ufw limit proto tcp from any port 22 (be care at the beginning 8080 is needed but better to configure a proxy o redirect 8080 to 443 / https)
Web Zugriff auf Jenkins:
Im Webbrowser unter http://your_server_ip_or_domain:8080
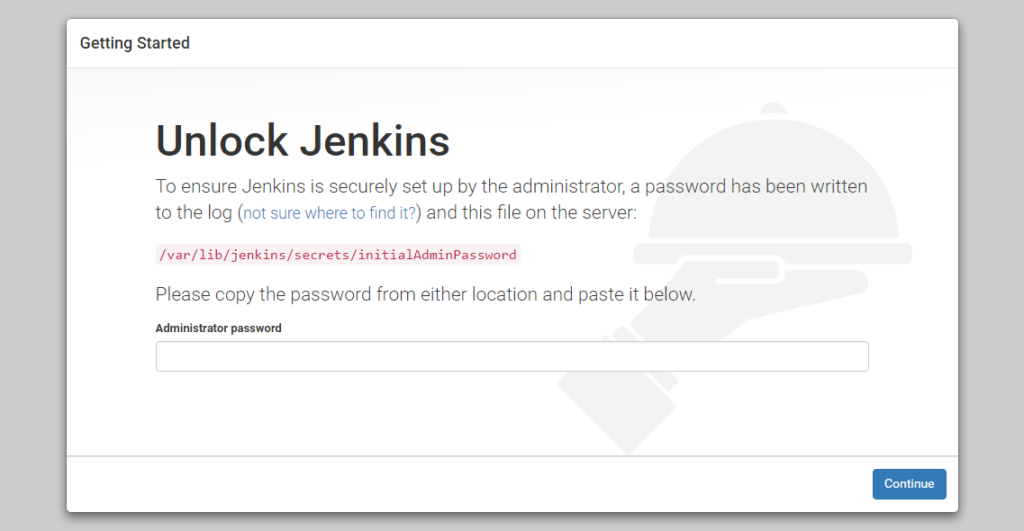
Im Terminal mit cat command dasiInitiale password ausgeben:
sudo cat /var/lib/jenkins/secrets/initialAdminPassword
Kopiere das Passwort und füge es in das Administrator password Feld ein und klick weiter
Das nächste Fenster bietet empfohlene oder ausgewählte Plugins zur Installation an
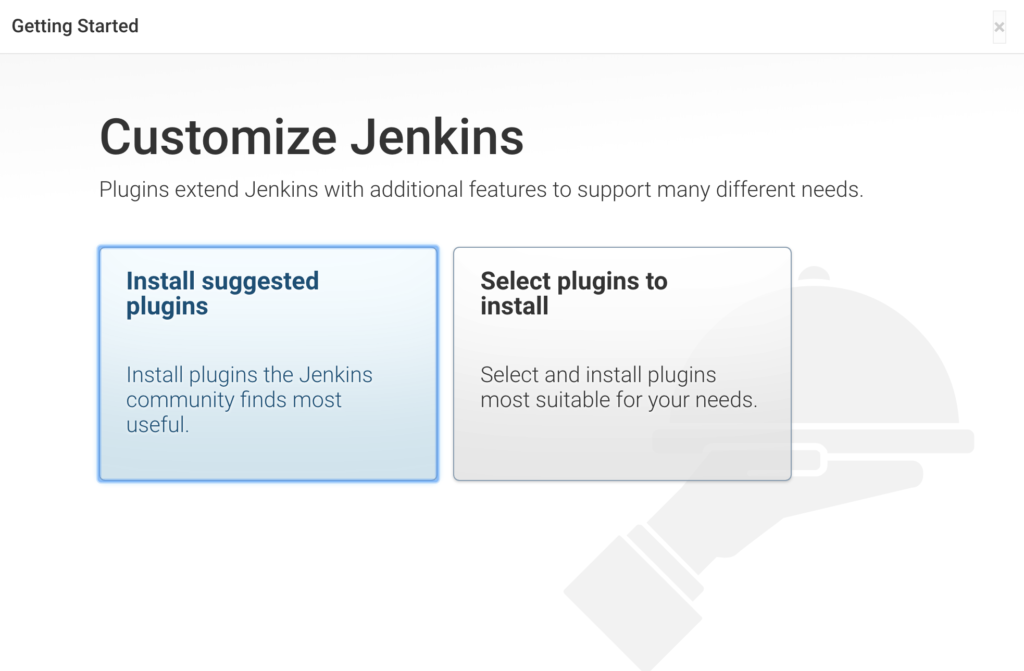
Wir wählen die empfohlenen Plugins aus und führe die Installation fort.
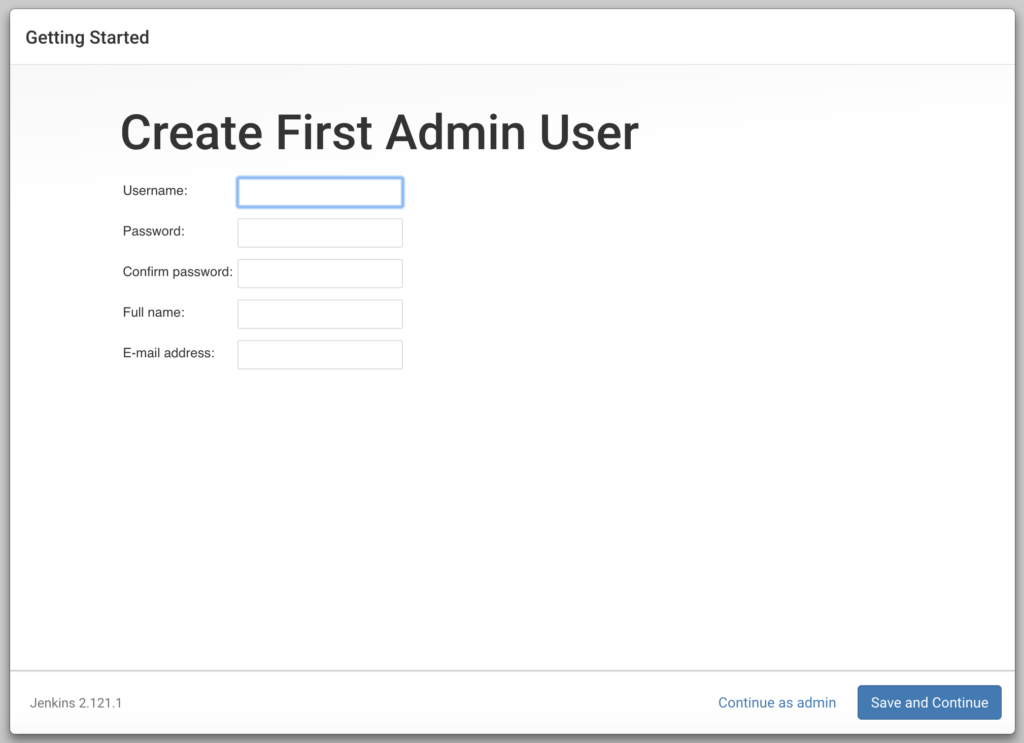
Nach der Installation wirst du nach einem Administrator Nutzernamen befragt. Hier kann man auch weiter gehen und als Standard „admin“ benutzten. Aber es ist Ratsam gleich einen eigenen anzulegen!
Die Übertragung der Passwörter ist standardmäßig nicht verschlüsselt, also lieber auf Https umstellen!
Anschließend muss nur noch die in Zukunft genutzte Url und Port bestätigt werden.
Danach ist die Installation abgeschlossen
Click Start using Jenkins um die jenkins Übersichtseite / Dashboard zu besuchen
Ändere Jenkins auf https mit proxy
install apache2
Füge einen virtual host zu der apache config hinzu
root@Host1:/etc/apache2/sites-enabled# cat jenkins-proxy.conf
<VirtualHost *:443>
ServerName jenkins.local.net
ServerAlias jenkins.local.net
SSLEngine On
SSLCertificateFile /etc/apache2/mycert/server.crt
SSLCertificateKeyFile /etc/apache2/mycert/server.key
ProxyRequests Off
ProxyPass / http://localhost:8080/
ProxyPassReverse / http://localhost:8080/
ProxyPassReverse / http://jenkins.local.net/
<Proxy http://localhost:8080/*>
Order allow,deny
Allow from all
</Proxy>
ProxyPreserveHost on
</VirtualHost>
Konfig Änderung für den passenden port 8080 ABER benutze den reverse proxy over apache um zum Port 443 umzuleiten!
root@HOST1:/etc/default# cat jenkins
# defaults for Jenkins automation server
# pulled in from the init script; makes things easier.
NAME=jenkins
# arguments to pass to java
# Allow graphs etc. to work even when an X server is present
JAVA_ARGS="-Djava.awt.headless=true"
#JAVA_ARGS="-Xmx256m"
# make jenkins listen on IPv4 address
#JAVA_ARGS="-Djava.net.preferIPv4Stack=true"
PIDFILE=/var/run/$NAME/$NAME.pid
# user and group to be invoked as (default to jenkins)
JENKINS_USER=root
# $NAME
JENKINS_GROUP=$NAME
# location of the jenkins war file
JENKINS_WAR=/usr/share/$NAME/$NAME.war
# jenkins home location
JENKINS_HOME=/var/lib/$NAME
# set this to false if you don't want Jenkins to run by itself
# in this set up, you are expected to provide a servlet container
# to host jenkins.
RUN_STANDALONE=true
# log location. this may be a syslog facility.priority
JENKINS_LOG=/var/log/$NAME/$NAME.log
#JENKINS_LOG=daemon.info
# Whether to enable web access logging or not.
# Set to "yes" to enable logging to /var/log/$NAME/access_log
JENKINS_ENABLE_ACCESS_LOG="no"
# OS LIMITS SETUP
# comment this out to observe /etc/security/limits.conf
# this is on by default because http://github.com/jenkinsci/jenkins/commit/2fb288474e980d0e7ff9c4a3b768874835a3e92e
# reported that Ubuntu's PAM configuration doesn't include pam_limits.so, and as a result the # of file
# descriptors are forced to 1024 regardless of /etc/security/limits.conf
MAXOPENFILES=8192
# set the umask to control permission bits of files that Jenkins creates.
# 027 makes files read-only for group and inaccessible for others, which some security sensitive users
# might consider benefitial, especially if Jenkins runs in a box that's used for multiple purposes.
# Beware that 027 permission would interfere with sudo scripts that run on the master (JENKINS-25065.)
#
# Note also that the particularly sensitive part of $JENKINS_HOME (such as credentials) are always
# written without 'others' access. So the umask values only affect job configuration, build records,
# that sort of things.
#
# If commented out, the value from the OS is inherited, which is normally 022 (as of Ubuntu 12.04,
# by default umask comes from pam_umask(8) and /etc/login.defs
# UMASK=027
# port for HTTP connector (default 8080; disable with -1)
HTTP_PORT=8080
# servlet context, important if you want to use apache proxying
PREFIX=/$NAME
# arguments to pass to jenkins.
# --javahome=$JAVA_HOME
# --httpListenAddress=$HTTP_HOST (default 0.0.0.0)
# --httpPort=$HTTP_PORT (default 8080; disable with -1)
# --httpsPort=$HTTP_PORT
# --argumentsRealm.passwd.$ADMIN_USER=[password]
# --argumentsRealm.roles.$ADMIN_USER=admin
# --webroot=~/.jenkins/war
# --prefix=$PREFIX
JENKINS_ARGS="--webroot=/var/cache/$NAME/war --httpPort=8080"
## with HTTPS !!!
# JENKINS_ARGS="--webroot=/var/cache/$NAME/war --httpPort=-1 --httpsPort=443"
Sperren des port 80 für mehr Sicherheit:
root@fba-mail:/etc/default# cat /etc/apache2/ports.conf
# If you just change the port or add more ports here, you will likely also
# have to change the VirtualHost statement in
# /etc/apache2/sites-enabled/000-default.conf
# Listen 80
<IfModule ssl_module>
Listen 443
</IfModule>
<IfModule mod_gnutls.c>
Listen 443
</IfModule>
Jenkins Plugins für CI/CD
Jenkins Plugins
============================================
AnsiColor
Build Monitor View
Build Name Setter
Build Timeout
Conditional BuildStep
Copy Artifact Plugin
Email Extension Plugin
GitHub Branch Source Plugin
Gradle Plugin
Green Balls
HTML Publisher plugin
Matrix Reloaded Plugin
Node and Label parameter plugin
Naginator
Pipeline Aggregator
Pipeline: GitHub Groovy Libraries
Pipeline: Groovy
Pipeline: Nodes and Processes
Role-based Authorization Strategy
SSH Agent Plugin
SSH Slaves plugin
Subversion Plug-in (Standard or dependency? o.O )
Text File Operations
ThinBackup
Timestamper
Workspace Cleanup Plugin
xUnit plugin